- Comparitech Stack Report
- Posts
- Blockchain Meets Cybersecurity: A New Investment Frontier at Black Hat 2025
Blockchain Meets Cybersecurity: A New Investment Frontier at Black Hat 2025


✍🏻 From the Editor’s Desk
New warnings about foreign access to U.S. critical infrastructure have reignited long-standing concerns over supply chain dependencies and embedded vulnerabilities. For security leaders, the question isn't whether the grid is at risk—it’s how deep the exposure runs and what visibility organizations really have into their operational systems
🔎 Deep Brief
Blockchain Meets Cybersecurity: A New Investment Frontier at Black Hat 2025
At Black Hat USA 2025, the convergence of cybersecurity and blockchain was a strategic highlight. This crossover marks a new innovation frontier: startups are building tools that merge smart contract auditing, DeFi risk modeling, and protocol security with blockchain-native compliance systems. Investors showed strong interest in ventures leveraging zero‑knowledge proofs, decentralized identity, and analytics platforms tailored to blockchain threat data. The event reinforced that cybersecurity is now a core part of blockchain infrastructure—not a separate layer—creating dual-use markets blending regulatory tech, risk analytics, and digital asset protection..
🧠 Strategy in Action
Marks & Spencer Breach Highlights Supply Chain Risks
Retail giant Marks & Spencer suffered a data breach after cybercriminals exploited a third-party service provider managing employee payroll. Attackers accessed personal data such as names, addresses, national insurance numbers, and bank details, affecting hundreds of current and former employees. The breach originated not within M&S systems but from the external vendor Zellis, which itself was compromised through a broader attack linked to the MOVEit file transfer vulnerability. This high-profile incident underscores how even well-defended enterprises can be exposed through interconnected service ecosystems.
In response, M&S promptly notified affected individuals, offered credit monitoring, and reassessed its third-party risk program. The company also worked with regulators and security partners to ensure ongoing compliance with data protection rules.
👉 Takeaway: Even strong internal security can be undermined by external vendors with unpatched vulnerabilities, so organizations need strong third-party risk assessment programs and processes.

Want weekly curated list of {Cyber,Info}Security insightful resources, links, and some other security & privacy things too?
⚖️ Regulation Radar
GAO and Industry Urge Unified Cybersecurity Standards Across Sectors
A new Government Accountability Office (GAO) report, supported by industry leaders, is pushing for a consistent set of cybersecurity rules across critical infrastructure sectors. Currently, regulations differ by industry—what applies to the energy sector may not apply to financial services or healthcare. This fragmented approach creates compliance confusion, leaves gaps, and slows down risk response efforts. GAO recommends that federal agencies coordinate with private-sector partners to align baseline cybersecurity standards and streamline incident reporting requirements.
What IT leaders should know.
Expect greater federal pressure for cross-sector alignment on security controls.
Incident reporting rules may be standardized across industries, shortening response windows.
Organizations in regulated sectors should begin reviewing overlaps in current frameworks (NIST, ISO, sector-specific rules).
Cross-functional compliance teams will become more important to manage upcoming changes.
🛠️ Tool Check
Top Patch Management Tools for 2025
Keeping systems updated is one of the simplest yet most neglected areas in security. Comparitech reviewed leading patch management tools based on automation, reporting, OS compatibility, and scalability
Top tools are:
NinjaOne Patch Management - A support tool aimed at managed service providers that patches Windows and Mac OS environments and is tuned to update 135 different software packages.
Atera Patch Management - A cloud-based patch manager designed for deployment by MSPs that includes patch availability searches and a dashboard that allows patch selection.
SuperOps Patch Management - Part of an RMM package, this service will patch endpoints running Windows. Delivered from the cloud.
ManageEngine Patch Manager Plus - A patch manager for Windows, Linux, and Mac OS that supports more than 750 applications.
PRTG Network Monitor - IT infrastructure monitor that also supervises software and operating system versions.
ESET Protect MDR - A fully managed cybersecurity package that includes threat detection and response, vulnerability scanning, and patch management.
🗣️ Community Signal
“Cyberattack costs aren’t just hitting businesses—they’re being passed down like a surprise surcharge at checkout. Think higher fees, costlier services, and maybe even that “convenience fee” you didn’t know existed.” Dr. Chase Cunningam..
📚 Don’t Miss This
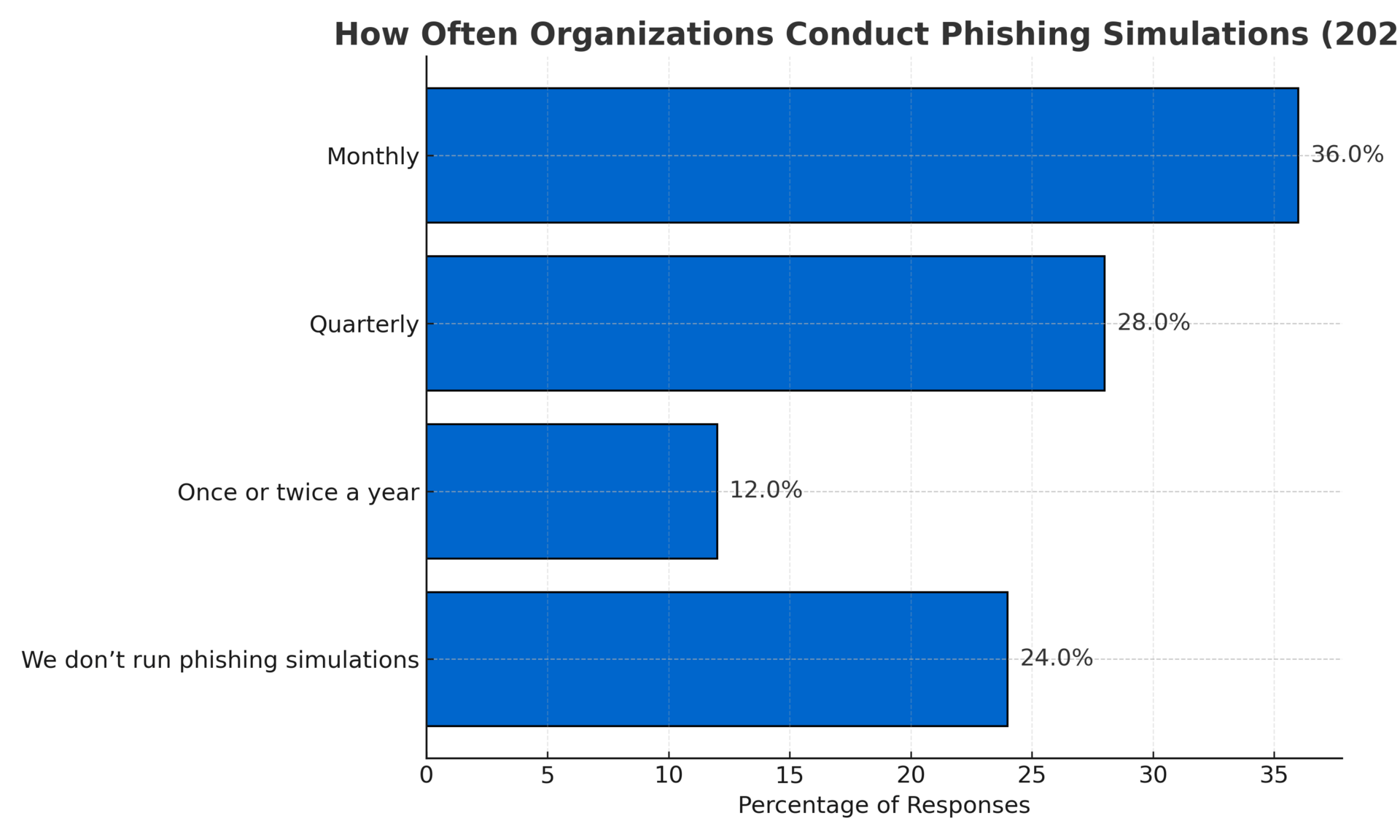
🗳️ Your Take - The Results
Poll Question: How often do you change your work passwords?
🔗 Stay Connected
Until next week!
