- Comparitech Stack Report
- Posts
- Businesses Underinvest in Cybersecurity
Businesses Underinvest in Cybersecurity

⚡ Weekend Threat Brief
Aflac Updates 2025 Security Incident
Aflac released a year-end update on the cybersecurity incident it first disclosed from June 2025, saying it has now completed a detailed review of the affected systems. The insurer found suspicious activity on its U.S. network that impacted personal information tied to roughly 22.65 million individuals, but there was no ransomware, and business systems stayed operational. Aflac contained the activity within hours, reset passwords for potentially affected accounts, and added monitoring to detect unusual activity. The company has begun notifying impacted individuals and continues to work with third-party security experts and law enforcement. So far, Aflac reports no known fraudulent use of the data.
Takeaway
Personal data of roughly 22.65 million individuals was potentially involved.
The incident was contained quickly with no ransomware detected.
Aflac has enhanced monitoring and account protections.
🎯 Tactical Playbook
2026 Cybersecurity Predictions
Industry forecasts for cybersecurity in 2026 point to rapid shifts driven by artificial intelligence, identity risks and advanced attacks. Experts agree AI will be used by both defenders and attackers, automating threat detection and threat creation, and creating new challenges like autonomous attack agents and hyper-personalized social engineering. Organisations are expected to prioritise zero-trust identity frameworks, secure-by-design practices, and AI-centric defences as breaches become more sophisticated. Other predictions highlight that deepfake tools, credential abuse and automated reconnaissance will drive breach strategies, making traditional perimeter defences less effective. Boards and CISOs must adjust investment and strategy to anticipate these emerging threat vectors rather than respond after breaches occur.
Takeaway
AI will be central to both cyberattack tactics and defence operations.
Identity security will become the core focus of enterprise cyber strategy.
Zero trust and secure-design practices will be widespread compliance drivers.
🛡️ Research Watch
Businesses Underinvest in Cybersecurity

This study shows that many businesses still do not spend enough on cybersecurity tools, updates and proactive vulnerability assessments. A significant number of small and midsize companies assign critical cybersecurity duties to underqualified staff, leaving them exposed to evolving threats. The research also found organisations are slow to update outdated systems and are not conducting regular testing to identify and fix weaknesses, which increases risk as attackers constantly refine methods. This underinvestment persists even as cyber threats grow more automated and sophisticated, underscoring the need for enterprises to align budgets with actual risk profiles and take proactive defensive measures.
🧩 Tool Tip of the Week
ThreatLocker for Access Control
ThreatLocker is a network access control (NAC) and endpoint security tool that helps organisations implement zero-trust principles by controlling which applications and devices can run or connect on a network. Use ThreatLocker’s application allowlisting feature to block unknown or risky software from executing, and pair it with ringfencing to limit what approved applications can do. This prevents lateral movement by attackers and reduces the risk from malicious code, especially in environments where remote work and BYOD are common. Combining strict access policies with regular reviews of allowed items can help maintain a hardened and visible security posture.
🗣️ Community Signal
One constant is that law firms are really high exposure for fraud, and that’s because the business model is based around sending payment requests constantly. So, attackers know if you compromise a lawyer’s inbox, you can just interject yourself and funnel funds. This is why law firms will always be high-risk. I guess what’s difficult is attackers will adopt different methods to perpetuate these frauds. So, the actual loss controls may change even though the industry class remains high risk. Daniel Woods, Lecturer at the University of Edinburgh.
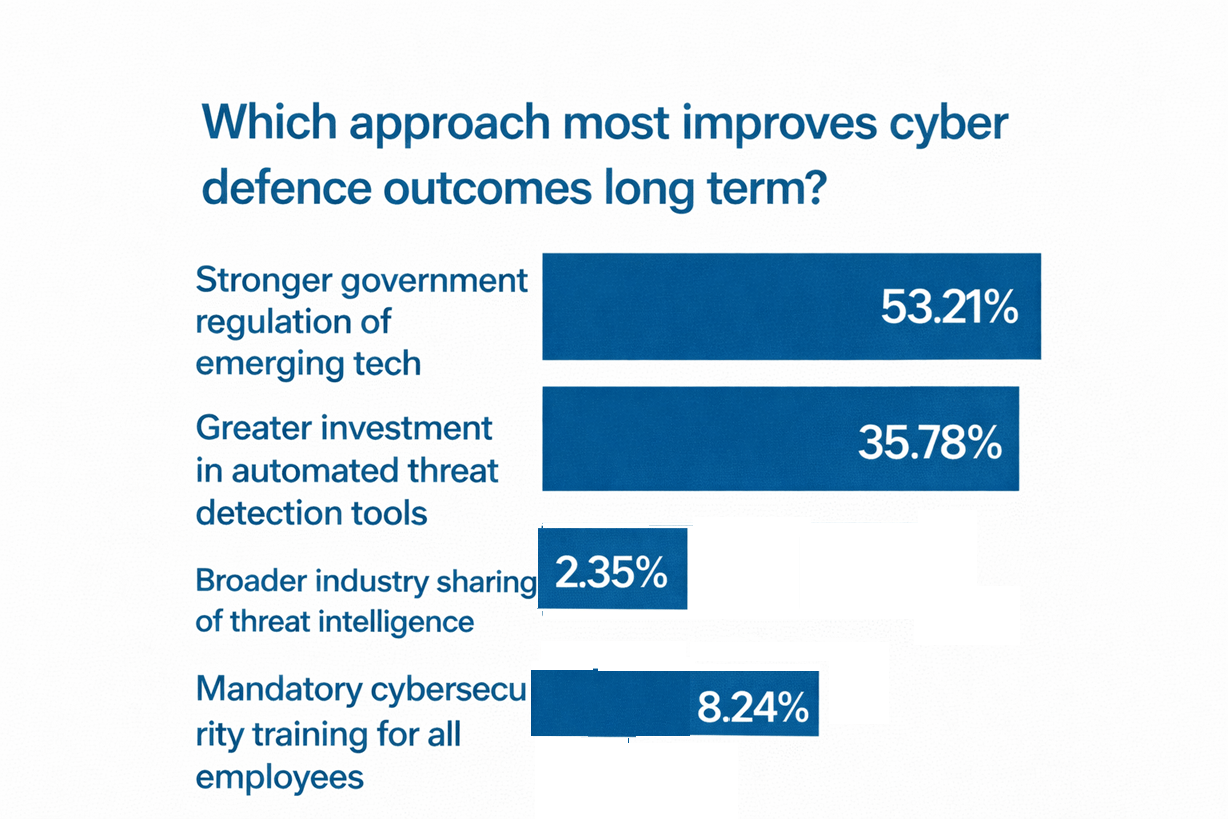
🗳️ Your Take - The Results
|
Until Monday’s edition - Let’s keep that zero-day count at zero!