- Comparitech Stack Report
- Posts
- China bans US and Israeli cybersecurity software in state systems
China bans US and Israeli cybersecurity software in state systems

⚡ Weekend Threat Brief
China bans US and Israeli cybersecurity software in state systems
China has moved to block the use of U.S. and Israeli cybersecurity products across key government and critical infrastructure networks. The new policy stipulates that technologies from foreign companies with ties to U.S. or Israeli governments may not be deployed on networks deemed essential for national security or economic stability. Experts see this as part of a broader push to reduce dependency on Western tech and build a domestic cybersecurity industry. The ban could disrupt multinational vendors and complicate future sales in the Chinese market. Security teams with global operations should monitor how this policy affects supply chain risk and compliance requirements.
Takeaway:
Export controls and geopolitical strategy now shape cybersecurity tool selection.
Global enterprises must review regional compliance with new software restrictions.
Supply chain risk increases when markets enforce national technology policies.
🎯 Tactical Playbook
Lessons from the Verizon outage remind us of network resilience gaps
A major Verizon network outage left millions without cellular coverage, spotlighting how dependent people and businesses are on a few dominant carriers. The outage disrupted emergency calls, banking apps, and connected services that rely on mobile networks. Experts highlight that organizations cannot assume constant connectivity and should plan for failures in public infrastructure. Tactical responses include multi-carrier failover plans, local Wi-Fi backups, and offline operational modes for mission-critical systems. The outage serves as a reminder that even large, robust providers can fail and that resilience planning must account for real-world interruptions.
Tactical tip:
Dependence on a single network provider creates systemic risk for operations.
Redundancy planning should include alternative carriers and fallback systems.
Testing operational resilience under degraded connectivity scenarios helps prevent business impact.
🛡️ Research Watch
Growing cyber-physical threats to U.S. energy infrastructure
Lawmakers and industry experts are increasingly concerned about cyber threats targeting U.S. energy systems, including power grids and critical distribution networks. Recent testimony pointed to both nation-state and criminal actors probing vulnerabilities in operational technology (OT) such as industrial control systems (ICS). Experts emphasised that traditional IT security measures are not sufficient for cyber-physical environments, which require specialized monitoring and response strategies. Federal agencies and private partners are advocating for stronger standards, increased information sharing, and targeted funding to bolster protection of energy infrastructure. As energy grids become more connected and digitized, attackers gain more opportunities to disrupt operations, raising national security and economic stability questions.
🧩 Tool Tip of the Week
Log Correlation from ManageEngine EventLog Analyzer
ManageEngine EventLog Analyzer is a powerful SIEM and log management tool that helps security teams collect, analyse, and correlate logs from across IT environments. To maximise its value: use real-time alert rules to catch suspicious events fast; configure correlation engines to link related alerts and reduce noise; and ensure logs are retained in line with compliance policies. The built-in reports for compliance standards help demonstrate control effectiveness during audits. Also, leverage custom dashboards to spotlight key risk indicators for your team. These steps make the tool not just a repository, but an active defence enhancer.
🗣️ Community Signal
We rarely talk about the moment after certification. The audit is closed. The findings are minor. The board relaxes. Security is “green.” And yet, this is often the point where organizations quietly lose steering power. Not because controls fail — but because ownership dissolves. Risk is documented, accepted, archived. Decisions move faster than governance. Certification proves that a system exists. It does not prove that it still shapes decisions. The uncomfortable question isn’t “Are we secure?” It’s “Who still feels responsible when the assumptions behind our controls expire?” Eckhart M, CISO - giz.
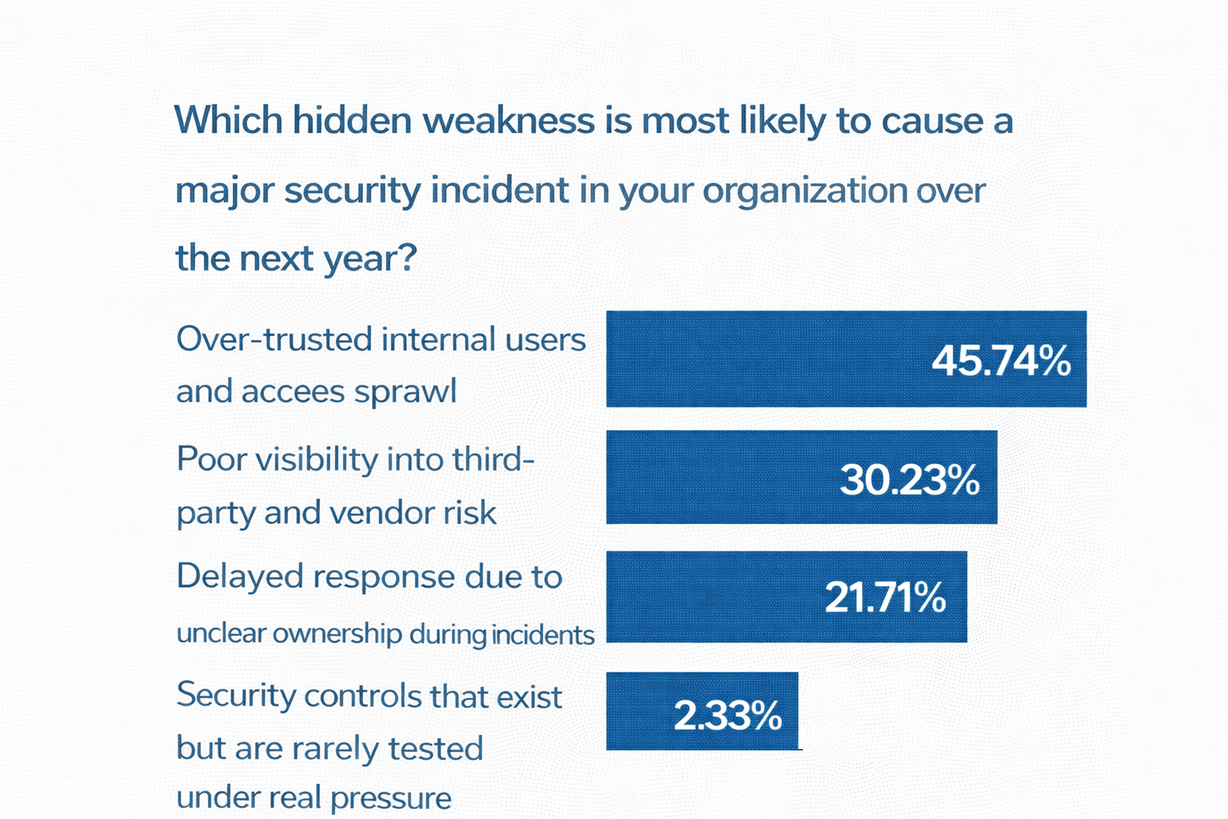
🗳️ Your Take - The Results
|
Until Monday’s edition - Let’s keep that zero-day count at zero!