- Comparitech Stack Report
- Posts
- Cisco Unified CM RCE actively exploited
Cisco Unified CM RCE actively exploited

⚡ Weekend Threat Brief
Cisco Unified CM RCE actively exploited
A critical remote code execution vulnerability in Cisco Unified Communications Manager (Unified CM) and related products has been actively exploited in the wild by attackers before a patch was released. The flaw, tracked as CVE-2026-20045, allows an unauthenticated threat actor to send crafted HTTP requests to the affected system’s web management interface, execute arbitrary commands and potentially gain full root access to the operating system. Cisco and security agencies are urging organizations running Unified CM, Unified CM SME, Unity Connection, IM & Presence and Webex Calling Dedicated Instance to apply the security fixes immediately. This vulnerability underscores ongoing risk where core communication infrastructure is exposed to attackers that do not need credentials to break in.
Takeaway:
CVE-2026-20045 is a critical remote code execution flaw that has been exploited before fixes were widely deployed.
Unauthenticated attackers can execute arbitrary commands and escalate privileges to root on affected systems.
The affected products include Unified CM, Unified CM SME, IM & Presence, Unity Connection and Webex Calling Dedicated Instance installations.
Immediate patching and access restriction to management interfaces are recommended to lower attack risk.
🎯 Tactical Playbook
The Case for U.S. Leadership Beyond UN Norms

The United States is moving toward a more unilateral and capability-driven cyber strategy, stepping back from long-standing participation in international cyber norm forums such as the UN Group of Government Experts and the Open-Ended Working Group. The current approach views these forums as slow, non-binding, and ineffective at deterring hostile cyber activity. Instead of consensus-based policy, the focus is shifting toward direct action, faster decision-making, and measurable deterrence. The strategy favors modernized cyber forces, stronger offensive readiness, and selective partnerships with aligned nations rather than broad multilateral agreement.
This shift is reflected in policy signals and funding decisions, including a major budget increase for U.S. Cyber Command and a renewed emphasis on offensive cyber capability in national strategy.
Key Takeaway:
The U.S. is deprioritizing UN-led cyber norm forums due to lack of enforcement and deterrence.
Cyber strategy is moving toward unilateral action supported by clear operational capability.
Increased funding for U.S. Cyber Command signals a focus on execution over diplomacy.
Offensive cyber capability is being positioned as a core part of national deterrence strategy.
🛡️ Research Watch
Who Trusts AI in Security Leadership?
A new survey of 500 CEOs and CISOs in the United States and United Kingdom finds a notable divide in trust toward AI tools used in cybersecurity. In the U.S., a large majority of both CEOs and CISOs express confidence in AI’s role in security decision-making, while leaders in the U.K. show far more skepticism. The study also shows that companies plan to increase cybersecurity spending even as they expect headcount changes driven by AI. These mixed views on AI trust and readiness could affect how organizations adopt new security technologies and address evolving threats.
🧩 Tool Tip of the Week
Monitoring with Paessler
Paessler PRTG Network Monitor is widely used for network and infrastructure monitoring, but it may not suit all needs. When evaluating alternatives, such as Paessler’s competition, ensure the tool offers flexible alerting, real-time performance dashboards and strong support for modern protocols. Choose solutions that scale easily across cloud and hybrid environments and allow customizable reporting to support different teams. Testing with your own traffic patterns can reveal how well each option detects real issues before deployment.
Tip: Use PRTG’s sensor groups to segment monitoring by function (for example servers, applications and security systems) so alerts stay relevant and actionable.
🗣️ Community Signal
Firewall makers join laptop, PC and smartphone vendors, all of which are expected to see big headwinds this year due to collapsing sales. DRAM prices have been up between 60% and 70% since last year and are expected to grow another 50% in the first quarter of the year alone. The production of most of this year's DRAM supply has already been purchased by AI companies for use in their future data centers. DRAM maker Micron has exited the consumer market and focused strictly on supplying AI and data center makers. South Korean company SK Hynix is also pondering a similar decision from both the DRAM and NAND SSD markets. Steve Gibson of SecurityNow podcast.
🗳️ Your Take - The Results
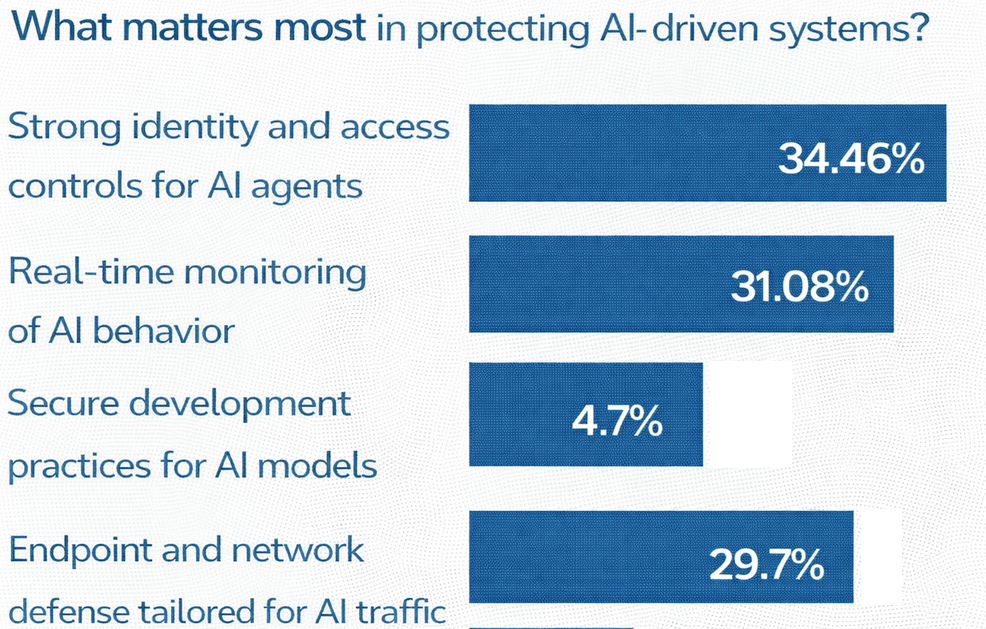
|
Until Monday’s edition - Let’s keep that zero-day count at zero!