- Comparitech Stack Report
- Posts
- CMMC Is Here: Why Manufacturers Must Act Now to Keep Defense Contracts
CMMC Is Here: Why Manufacturers Must Act Now to Keep Defense Contracts

⚡ Weekend Threat Brief
CMMC Is Here: Why Manufacturers Must Act Now to Keep Defense Contracts
The Cybersecurity Maturity Model Certification (CMMC) has moved from proposal to enforcement. As of November 10, 2025, the DoD will begin enforcing CMMC clauses in new defense contracts. Manufacturers and defense suppliers must prepare — the window to act is closing.
Key points
Conduct assessments aligned to CMMC 2.0 levels.
Engage certified third-party assessors (C3PAOs) early.
Remediate gaps in identity, logging, control systems ahead of time.
Rework contracts and sub-contractor obligations to include CMMC compliance.
Takeaway: If you handle or intend to handle DoD work, this shift is no longer optional — it’s a barrier to entry.
🎯 Tactical Playbook
Microsoft: Russia, China Increasingly Using AI to Escalate Cyberattacks on the US
Russia, China, Iran, and North Korea are adopting AI tools to automate and scale their cyber operations. In July 2025 alone, Microsoft identified over 200 instances of AI-enabled disinformation and deepfake activity — more than double the prior year.

Tactics in play now:
AI-driven phishing that sounds more natural
Digital clones of officials to penetrate defenses
Using AI to craft deceptive narratives or social engineering campaigns
Tactical tip: Defenders must sharpen basic cyber hygiene now — advanced tools won’t matter if the foundation is weak.
🛡️ Research Watch
“End Cybersecurity” — Rethinking Defence in U.S. Policy
Foreign Affairs discusses a provocative view: rather than chasing perfection in cybersecurity, the U.S. might shift to absorbing certain cyber harms and focusing more on deterrence, resilience, and strategic offense.
Highlights
The limits of perfect defense — total prevention is impossible
The case for stronger cyber deterrence and attribution
Emphasis on recovery, repair, and strategic posture over reactive patching
This kind of thinking could influence national policy and funding — worth watching for shifts in how defensive strategy is framed.
🧩 Tool Tip of the Week
NinjaOne: Leverage Unified Monitoring to Speed Incident Detection
From the Comparitech survey of RMM tools: NinjaOne stands out for its unified dashboard and automatic alerting features. It allows admins to view endpoint status, patch compliance, and performance metrics in one interface.
Configure high-severity alerts for CPU spikes, memory usage, and service failures
Use built-in scripting or remote terminal to triage issues immediately
Link NinjaOne alerts to your ticketing or incident system to close response loops
This setup ensures you catch trouble early and reduce dwell time.
🗣️ Community Signal
Regulation that treats AI like weapons creates explicit trade-offs: if you make it hard to build models and start companies, you can’t complain when innovation happens elsewhere. Benedict Evans.
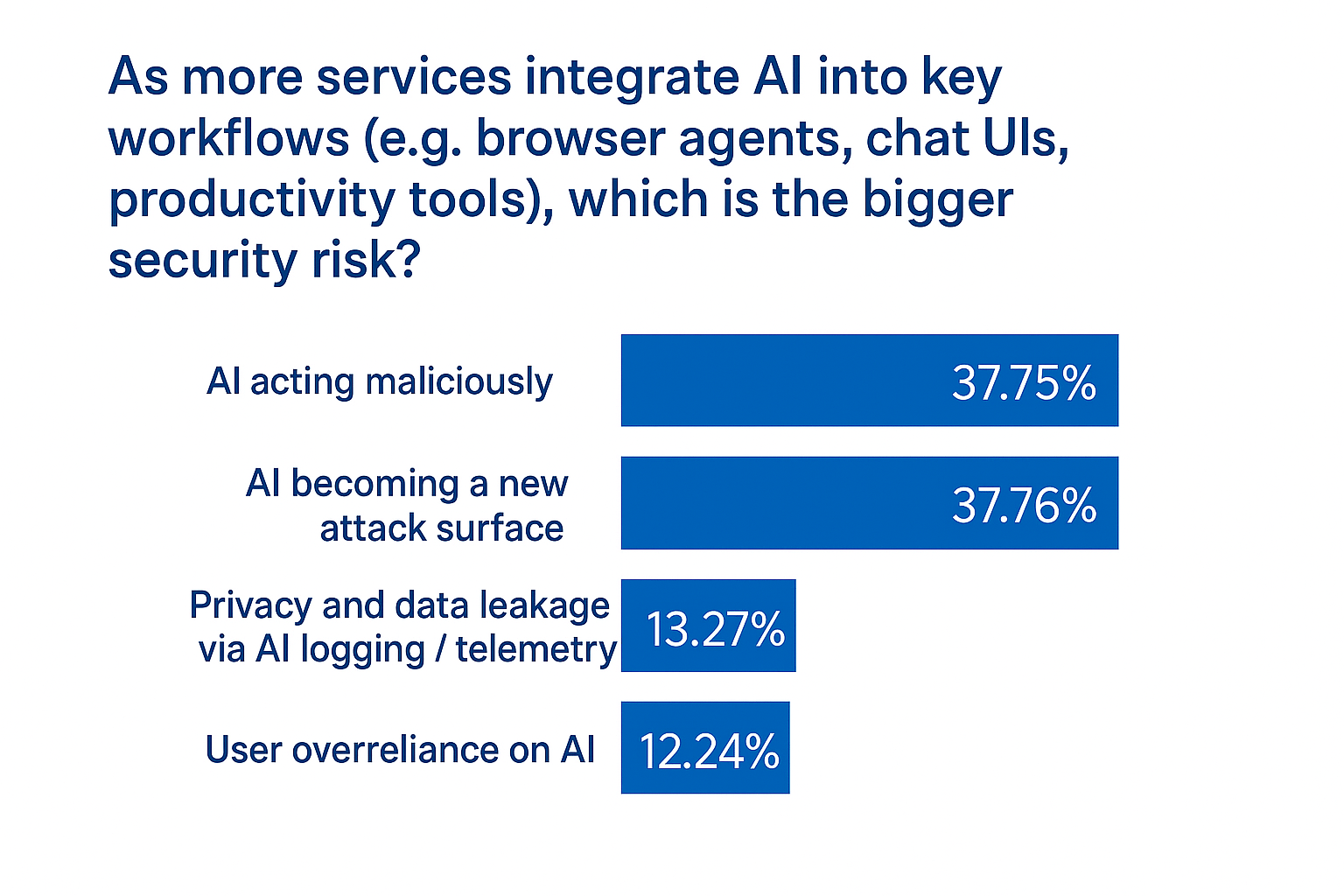
🗳️ Your Take - The Results
AI acting maliciously and AI becoming a new attack surface have garnered the maximum votes, with the former edging the latter by just one extra vote!.
|
Until Monday’s edition - Let’s keep that zero-day count at zero!