- Comparitech Stack Report
- Posts
- Hackers claim breach of HSBC USA exposing customer financial records
Hackers claim breach of HSBC USA exposing customer financial records

⚡ Weekend Threat Brief
Hackers claim breach of HSBC USA exposing customer financial records
A hacker group has claimed responsibility for breaching HSBC USA, allegedly exposing sensitive customer data, including bank account details and financial records. The attackers posted samples of the stolen data on underground forums, claiming it came from internal HSBC systems. The bank has yet to confirm the scope of the incident, but initial investigations suggest that customer contact information, transaction data, and partial account numbers may have been accessed.
Cybersecurity analysts believe this breach could be part of a broader campaign targeting global financial institutions through credential theft and API exploitation. If verified, the breach could have serious regulatory and reputational consequences for HSBC.
Takeaway: Customers are being advised to monitor their accounts for unauthorized activity and change online banking passwords immediately. The incident highlights the growing risk of financial data theft and the need for stronger identity and access management within banking networks.
🎯 Tactical Playbook
US government moves closer to banning TP-Link routers on national-security grounds
The US government is preparing to take action against TP-Link, citing security concerns about its hardware supply chain. Lawmakers are considering adding TP-Link to the Federal Communications Commission’s “covered list,” which would effectively ban the sale and use of its routers in government or critical infrastructure networks. Officials argue that the company’s close ties to Chinese entities pose a national security risk. TP-Link has denied these allegations, stating that its devices meet all regulatory standards. If approved, the ban would mirror previous restrictions on Huawei and ZTE.
Tactical tip: Cyber experts warn that this could disrupt procurement processes for agencies and smaller contractors relying on affordable networking gear.
🛡️ Research Watch
Keeper Security report highlights AI and identity security gaps
Keeper Security’s latest research reveals troubling global cybersecurity weaknesses, particularly in identity management and AI-related threats. The study found that 95% of organizations faced at least one identity-based attack in the past year, while 82% believe AI-generated phishing will increase risk in 2025. The report highlights that many companies still lack zero-trust policies, leaving credentials and privileged access exposed. It also found that security budgets are failing to keep pace with the sophistication of emerging threats. Experts recommend prioritizing passwordless authentication, user behavior analytics, and stricter access controls. The findings underscore how rapid AI adoption, without parallel investment in identity protection, can amplify systemic risks.
🧩 Tool Tip of the Week
Mastering network visibility with Auvik
Auvik continues to be a favorite among network administrators for its clarity and automation. This cloud-based network monitoring platform discovers, maps, and monitors devices using SNMP and other standard protocols, offering instant visibility across complex infrastructures. It simplifies troubleshooting and reduces downtime by showing real-time device health, performance metrics, and topology maps.
Tips for using Auvik effectively
Use automated discovery: Let Auvik scan your network to detect all connected devices—ideal for multi-site visibility.
Set smart alerts: Configure alerts for bandwidth spikes, device disconnections, or unusual traffic to detect issues early.
Monitor configuration changes: Track switch and router configurations to prevent unauthorized changes.
Leverage remote management: Access network devices securely without a VPN, saving time on site visits.
Auvik’s intuitive dashboard and automation tools make it a strong choice for MSPs and IT teams managing distributed environments.
🗣️ Community Signal
From a bigger picture standpoint, you want to leverage your custodians, your custodial relationship. They all have tools that they provide and can help from a compliance perspective, whether those are exception reports, trade reports—and don't forget you also most of them have discounts for other vendors—so whether it's proxy services or really a whole host of items, you want to become familiar with that, you want to stay on top of the reporting capabilities, and...you also have the NSCP.. Bart McDonald from Renaissance Regulatory Services.
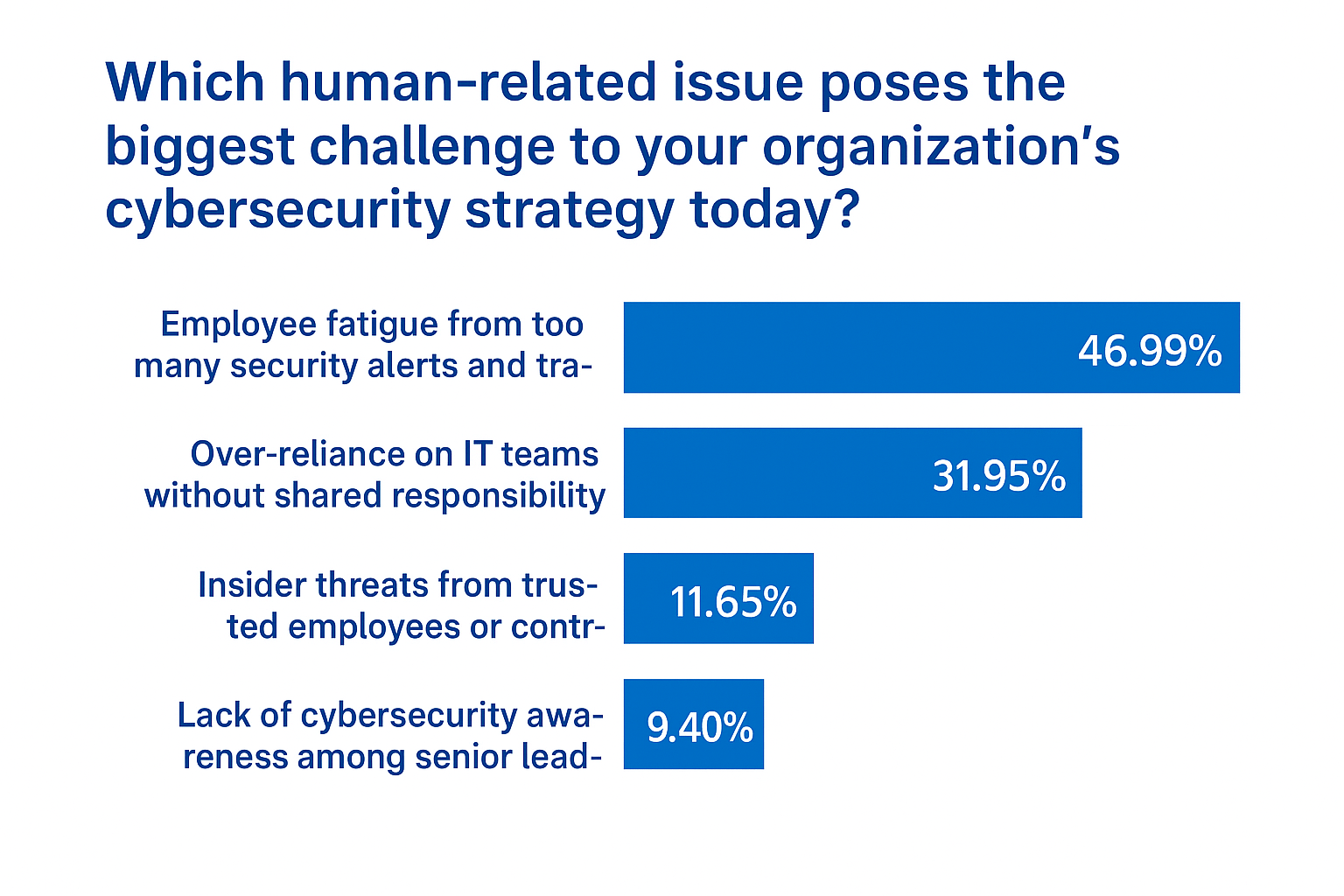
🗳️ Your Take - The Results
Employee fatigue tops our list of human-related issues, followed by over-reliance on IT teams.
|
Until Monday’s edition - Let’s keep that zero-day count at zero!