- Comparitech Stack Report
- Posts
- Sanctions Strike at Russian “Bulletproof” Host
Sanctions Strike at Russian “Bulletproof” Host

⚡ Weekend Threat Brief
Sanctions Strike at Russian “Bulletproof” Host
The U.S., U.K., and Australia have imposed coordinated sanctions on Media Land, a Russian web-hosting provider accused of facilitating ransomware operations by offering “bulletproof” infrastructure for cybercriminals.

Authorities argue that Media Land’s services allow threat actors to operate with impunity, helping them evade law enforcement while launching attacks. Sanctions target the company’s leadership and sister firms like ML.Cloud, freezing assets and banning business with sanctioned entities.
This move underscores how financial and regulatory tools — not just cybersecurity operations — are increasingly used to disrupt ransomware infrastructure
Takeaway: Sanctions are now a frontline tool in cyber defense, targeting the backbone that supports ransomware groups.
🎯 Tactical Playbook
AI-Powered Hackers for HireAI-Powered Hackers for Hire
A startup called Twenty (XX) — founded by former military hackers — has secured contracts to provide the U.S. military with AI tools to automate cyber-offensive operations. Their platform uses AI to accelerate reconnaissance, vulnerability discovery, and “break-in” planning — making military cyber operations more scalable and efficient.
This marks a shift in cyber warfare doctrine: not just defending, but giving cyber operators “scripts” and speed to disrupt adversary networks.
Tactical tip: AI is being weaponized for offense, not just defense — and the military is betting big on automation to amplify cyber power.
🛡️ Research Watch
FCC Plans to Roll Back Post–Salt Typhoon Cyber Rules
The FCC is set to rescind cybersecurity rules imposed on U.S. telecoms after the “Salt Typhoon” hacking campaign, arguing the earlier regulations overreached and weren’t flexible enough for real-world practice.
These rules initially required telecom operators to maintain a formal cybersecurity risk-management plan and report on it annually. Opponents warn that the rollback could weaken protections against state-backed espionage and undermine accountability in telecom infrastructure.
🧩 Tool Tip of the Week
Monitoring Logs with Paessler PRTG
Paessler’s PRTG Network Monitor includes built-in syslog receivers, letting you collect, filter, and alert on log data in real time.
A useful trick: Set up custom filters for specific log levels (e.g., ERROR, WARNING) so you don’t get overwhelmed by “noise” and only see the most critical issues. Also, use PRTG’s notification triggers — email, SMS, or webhook — tied to log-based sensors. That way, if a suspicious event appears in your logs, your team can act immediately.
Implementation tip: PRTG isn’t just for network metrics — it’s a powerful tool for real-time log monitoring when configurations are tailored well.
🗣️ Community Signal
One thing keeps standing out is that most breaches don’t happen because the attacker was a genius. They happen because someone left a door cracked open. Whether it’s outdated patches, weak passwords, poor segmentation, or overlooked logs, the smallest gap becomes the biggest risk. Greg Garcia, Dylan Spence, Security Researcher and Writer.
🗳️ Your Take - The Results
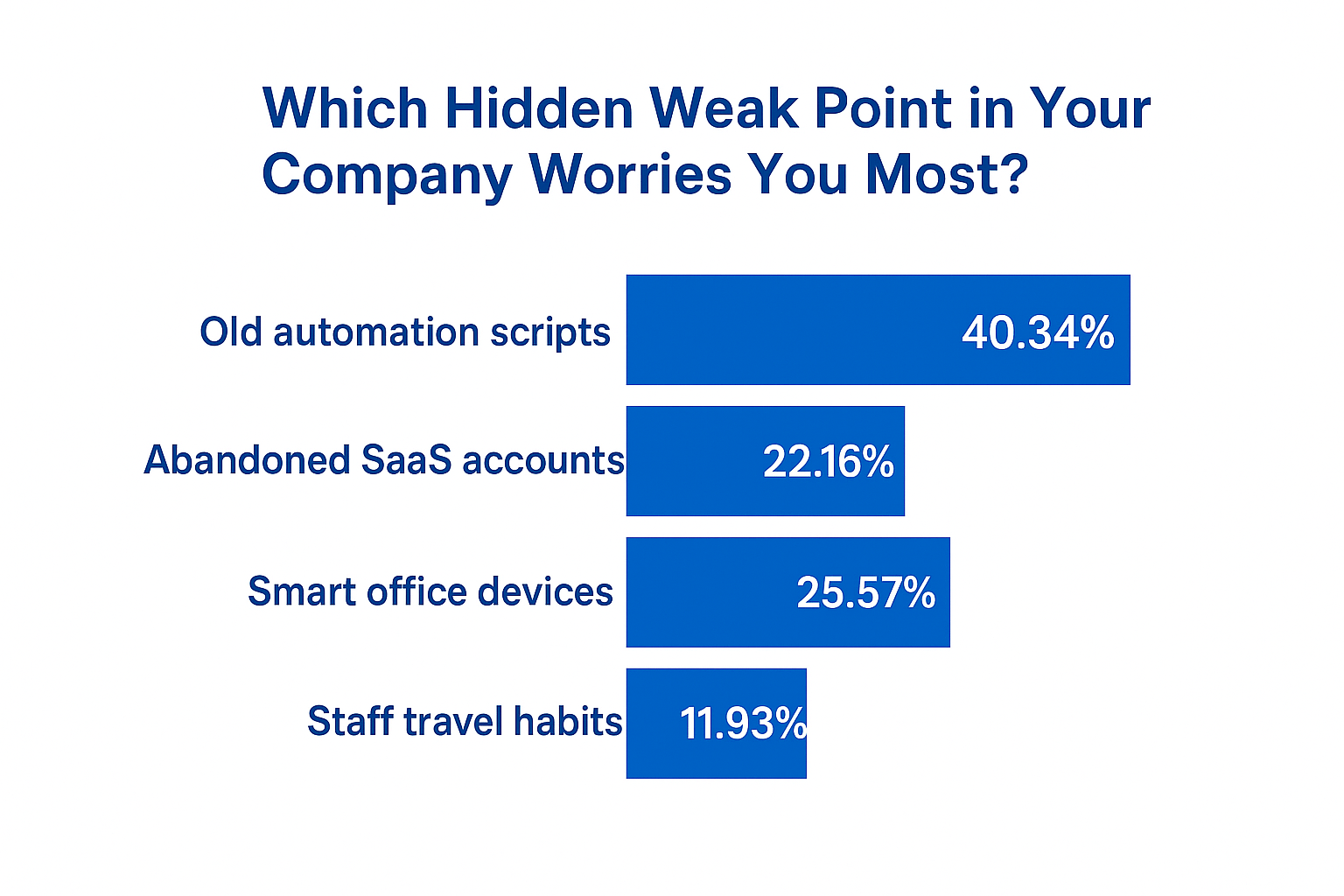
|
Until Monday’s edition - Let’s keep that zero-day count at zero!